Most of the previous write-ups focused on individual DPRK accounts on Github and their intricate connections, forming ‘clusters of activity’ in relation to the ‘IT Worker’ scheme. Today, we want to talk in more detail about the specific phenomenon of North Korean-established and maintained Github organizations. We’ll discuss a few examples found in the wild and evaluate the purposes of these often suspicious-looking Github organizations.
Why does the DPRK run its own organization?
We will focus on describing organizations we believe to be fully operated by the DPRK. The purpose of each one differs slightly, but in the end, they always serve as a ‘hub of activity’ for the accounts involved, facilitating multiple types of operations, including:
- Credibility building
- A central point for managing codebases between DPRK IT Workers
- Potential malware spreading
- Recruitment fronts (Both to acquire jobs and hire potential facilitators)
- Rug-pulling / Scamming
It’s hard to say how many such organizations exist. They often tend to be deleted after discovery, re-named, or simply abandoned. However, new ones quickly pop up and continue to be seeded with bogus activity, most often around cryptocurrencies or AI, or both at the same time.
One of the examples was already discussed in the past - the m8s-lab organization, which was comprised fully of DPRK operatives and a potential Canadian facilitator. Since the time of writing, one of the members has left, and development on public repositories has stopped. However, digging more into the tactics, techniques, and procedures of Github identities connected to m8s-lab, we can easily spot a few oddities:
- All repo code is appropriated from legitimate projects and presented as original.
- All developers are involved in “job begging” (relentless spam posts under Twitter job offers) and frequent nickname changes on social media (often because of bans imposed by Twitter and other platforms).
- Inflated follower and star counts to help the organization look more credible (the same tactic is applied outside of Github, e.g., Twitter or YouTube followers, fake Discord members).
The organization is additionally used as a front to recruit facilitators - people who knowingly or unknowingly help North Koreans get jobs, accept payments, or set up new fake identities. At least one person in the m8s-lab team fits the usual profile of a facilitator. And, the HyperbuildX organization, before its deletion, was also actively engaging job-constrained developers with offers of co-operation.
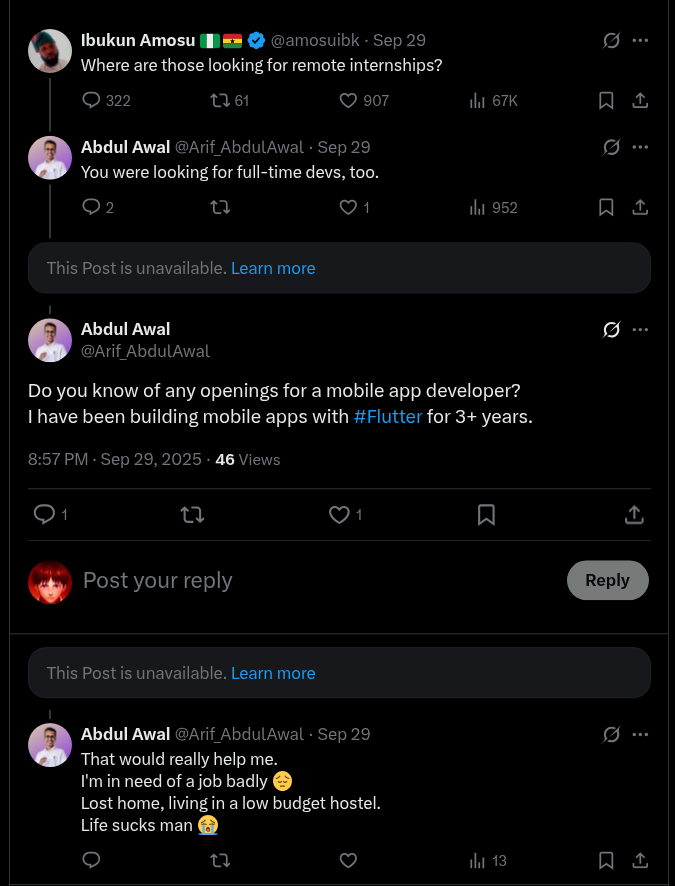
Additionally, the owner of m8s-lab - microgift88 - has a long history of using fake identities to gain employment in Web3 companies. Moreover, microgift88 was expanding his activity to both low-impact bug submissions on different contest platforms as well as at least one ‘rugpull’ project in the past.
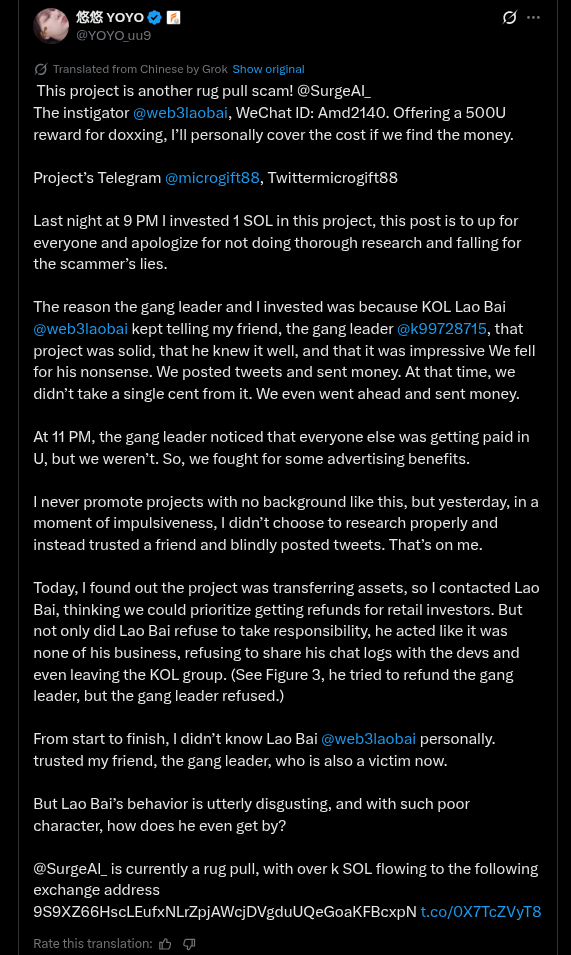
Meet HyperbuildX - A DPRK Scam Organization
NOTE: HyperbuildX was deleted from Twitter on 01/10/2025.
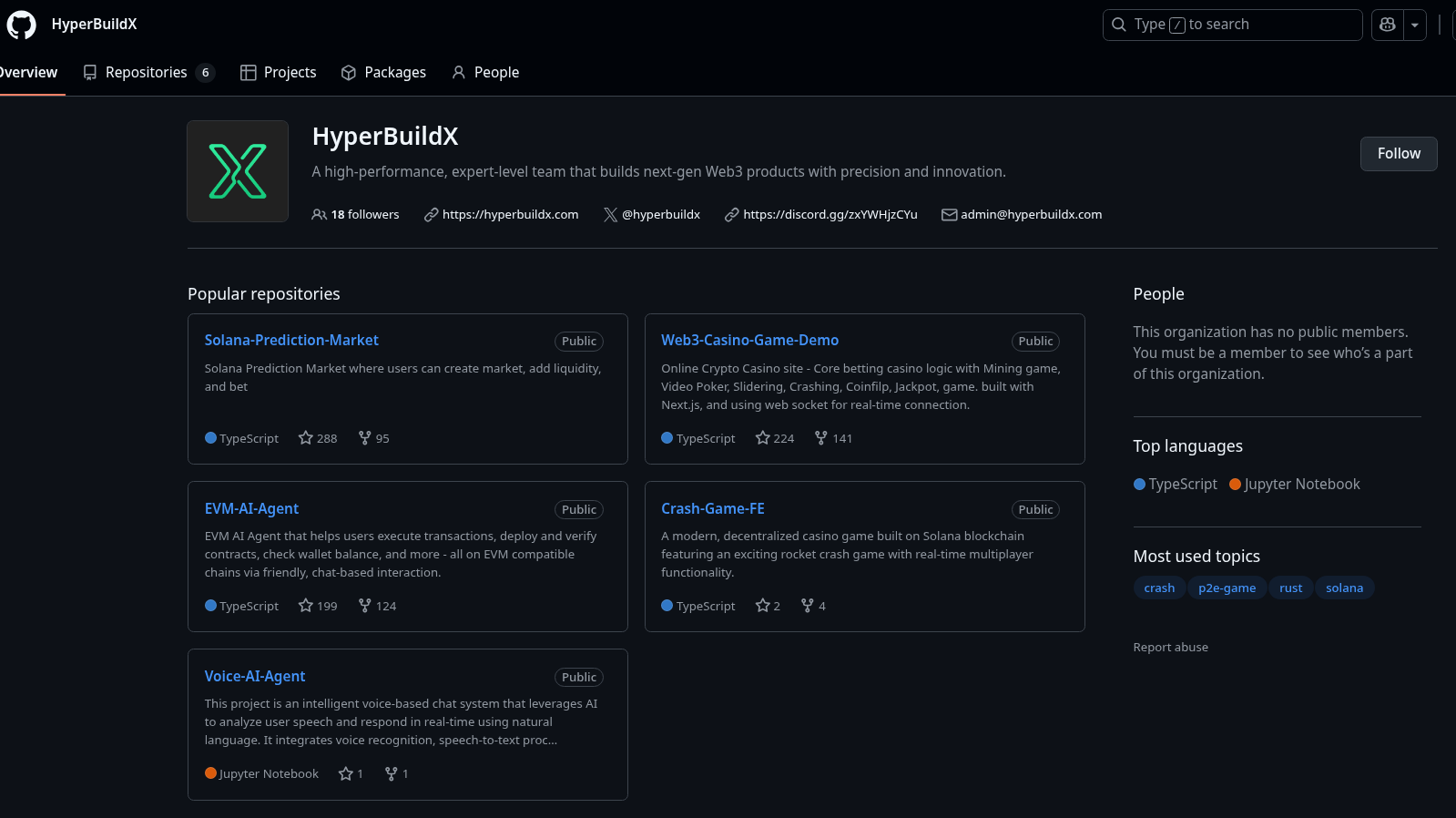
Same as the previously discussed m8s-labs, HyperbuildX is fully operated by DPRK IT Workers. A few similarities, as well as connections, exist between HyperbuildX and m8s-labs.
First of all, both operate as fake outsourcing agencies for a team of DPRK developers. Secondly, both seem to be oriented toward impersonating Solana-related development. Additionally, the strategy of ‘boosting’ accounts orbiting the organization is deployed by both projects.
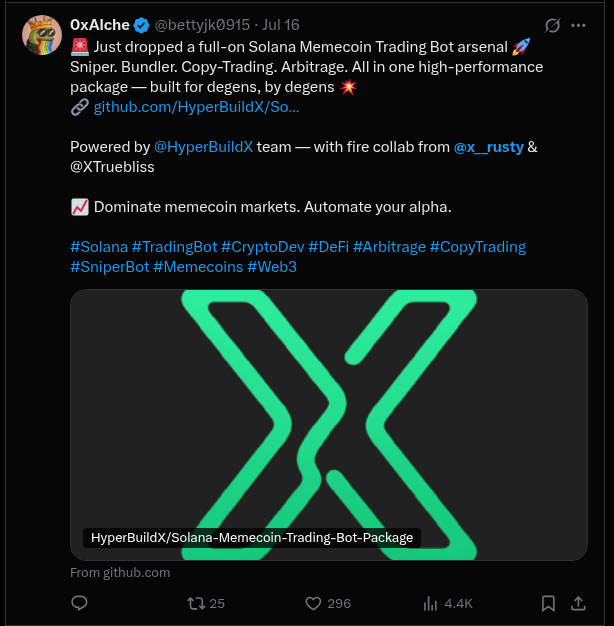
The main theme, so beloved by DPRK IT Workers, is trading bots, AI x Crypto automation, and casino/lottery-type dApps. For this goal, some of the workers even run their own YouTube channels explaining the functionalities of their trading bots (of course, all use AI-generated voices).
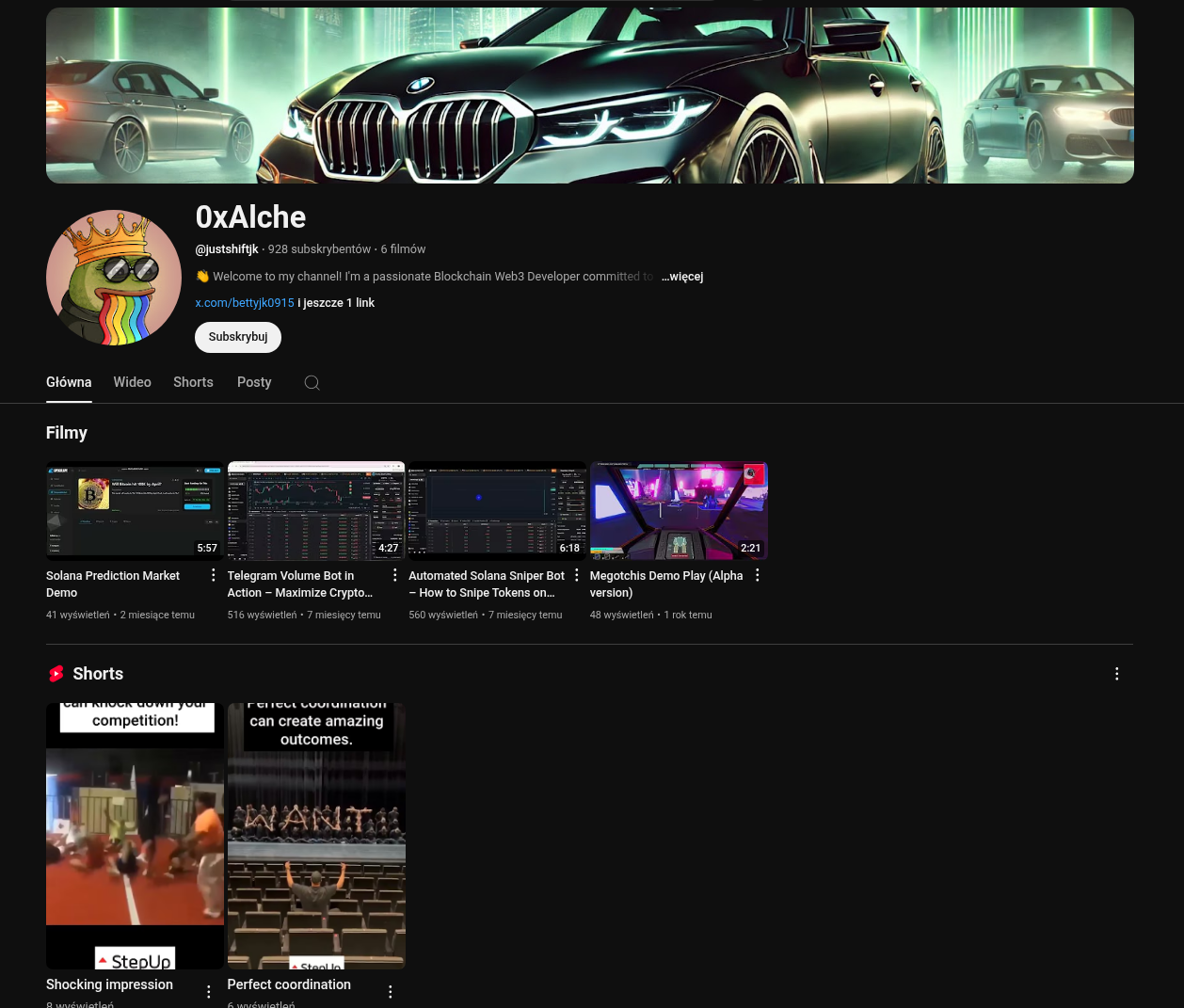
The organization focuses on ‘boosting’ the accounts of its main (DPRK) contributors, including actively recommending and vouching for them in the classic ‘job begging’ posts.
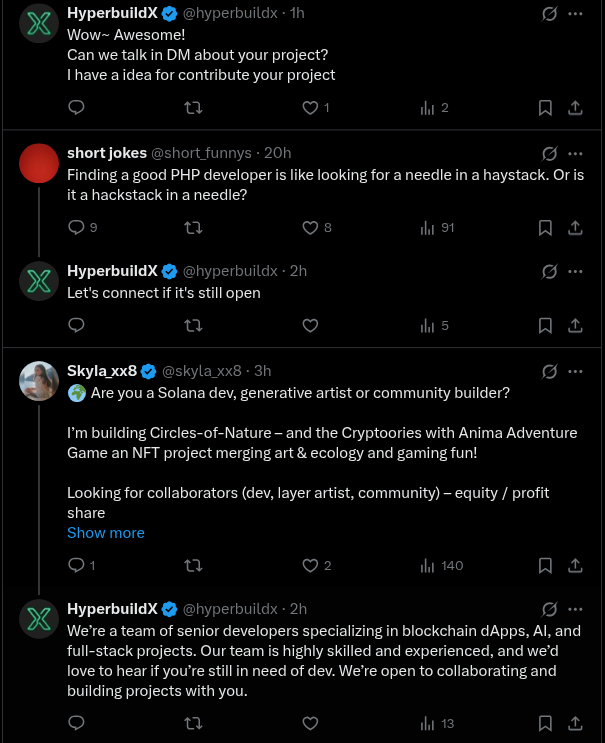
Solana development is, however, not the only service HyperbuildX is offering; in many different job-begging posts, we can see the organization offering development across different tech stacks.
The previously mentioned connection between m8s-labs and HyperbuildX is visible in the case of m8s-lab’s member XTruebliss - who since that time has had his accounts suspended and is now operating under https://x.com/0xMuseNine. The said actor can also be found being boosted by both HyperbuildX as well as AnotherRusty and justinshiftjk together (core members of Hyperbuildx).
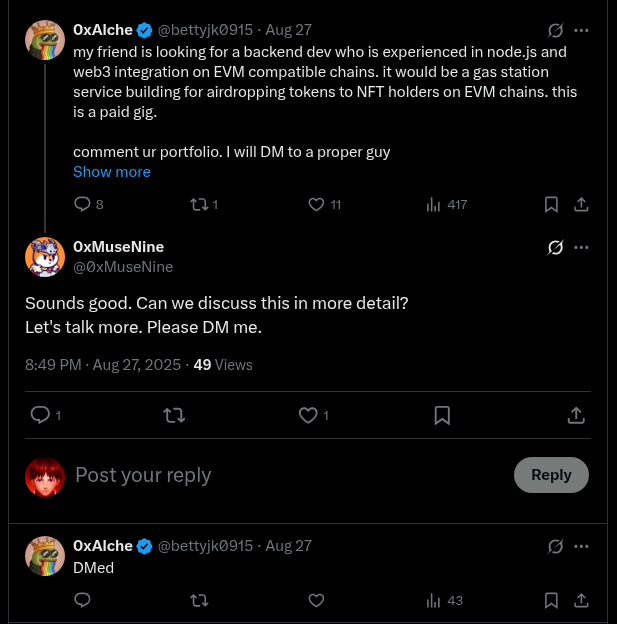
We can also see bot-like accounts amplifying DPRK IT Workers - all of the mentioned accounts are connected to DPRK IT Worker schemes, not only through HyperbuildX but also individually. Some of the workers mentioned in the below post were already publicly called out.
Similarly to justinshiftjk, at least one of the mentioned actors also operates a personal YouTube channel with a similar type of content.
The Core Team of HyperbuildX
Accounts from the below list are most likely operated by a single worker - AnotherRusty.
- adamglab0731.pl@gmail.com: justshiftjk (Also known as 0xAlche or Adam Glab)
- apollum.today@gmail.com: apollotoday (Also known as AnotherRusty or Matthias Li)
- hudes0112@gmail.com: m4rcu5o (Also operated by apollotoday)
- mufasa030831@gmail.com: Cornel
- keigo263129@outlook.com: Adrian
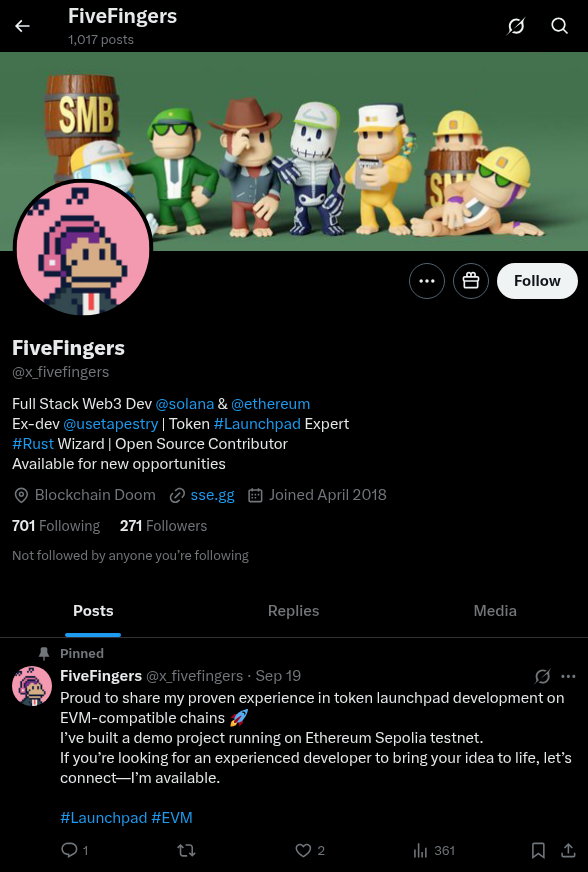
AnotherRusty
AnotherRusty most recently used the fake name of Matthias Li. That’s also how he gained employment in at least one blockchain company. What’s unique about AnotherRusty is how many accounts he operates, taking care to maintain high activity on each one of them. Below we present the real physical appearance of AnotherRusty, who claimed to be a US citizen.

Persona 1 (Matthias Li)
Github: https://github.com/AnotherRusty
Other names: rustynail015, rusty015, Solust_Rusty
Discord: rusty102 / 397440130744320035
Telegram: idioRusty
Telegram URL: https://t.me/anotherrusty
Email: nailrusty.dev@gmail.com
Email: matthiasli.mt@gmail.com
Name & Address (Fake): Mathias Li
Address: 4515 Coronado St. Greeley, CO 80634
Other (Fake) Name: Matthias Tovar
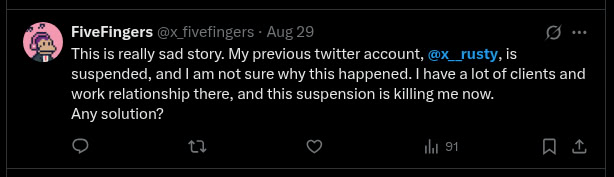
Twitter (suspended): https://x.com/x__rusty
Twitter (active): https://x.com/x_fivefingers
Personal Portfolio: https://www.matthiasli.com/
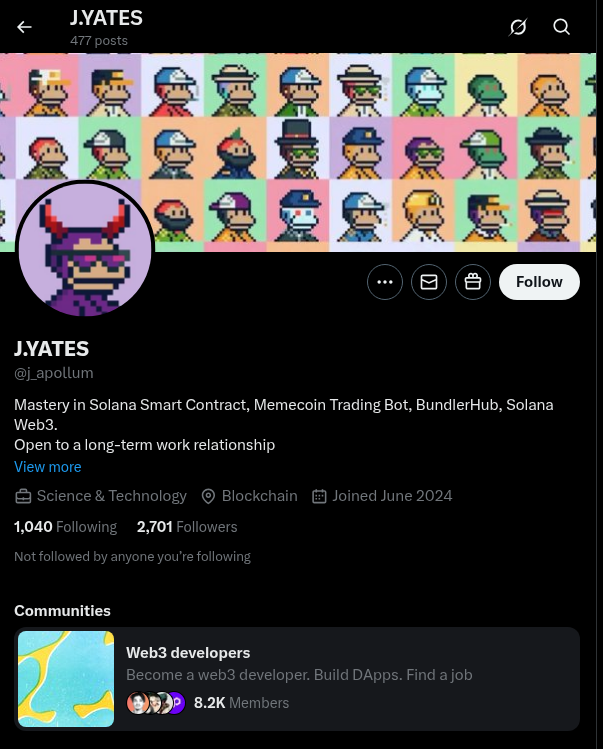
Persona 2 (apollotoday)
Github: apollotoday
Other names: SolMatts, MtBotDev, Apollum
URL: https://github.com/apollotoday
E-mail: matthiasli.mt@gmail.com
Twitter: https://x.com/j_apollum
Persona 3 (m4rcu5o)
Github: https://github.com/m4rcu5o
Other Names: Hudesdev, husreodev, MacSolDev, PupSol
E-mail: hudes0112@gmail.com
Telegram: https://t.me/idioRusty (shared with AnotherRusty)
Old Telegram: itsmyturn93
Twitter (active): https://x.com/m4rcu5o
Portfolio: matthiasli.com (shared with AnotherRusty)
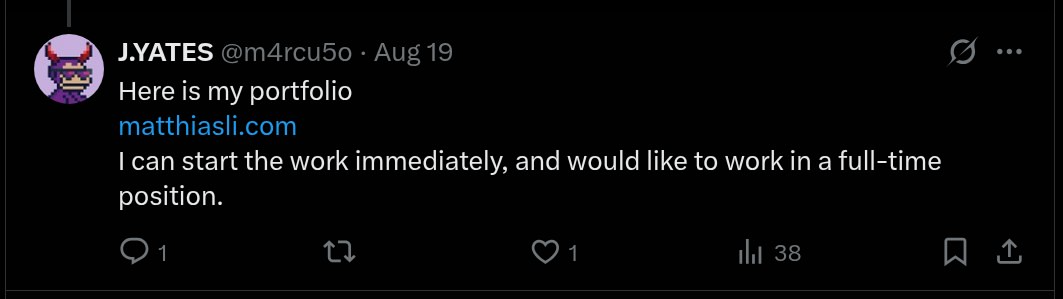
Moreover, m4rcu50o’s Calendly uses the same name as AnotherRusty: https://calendly.com/nailrusty-dev/30min
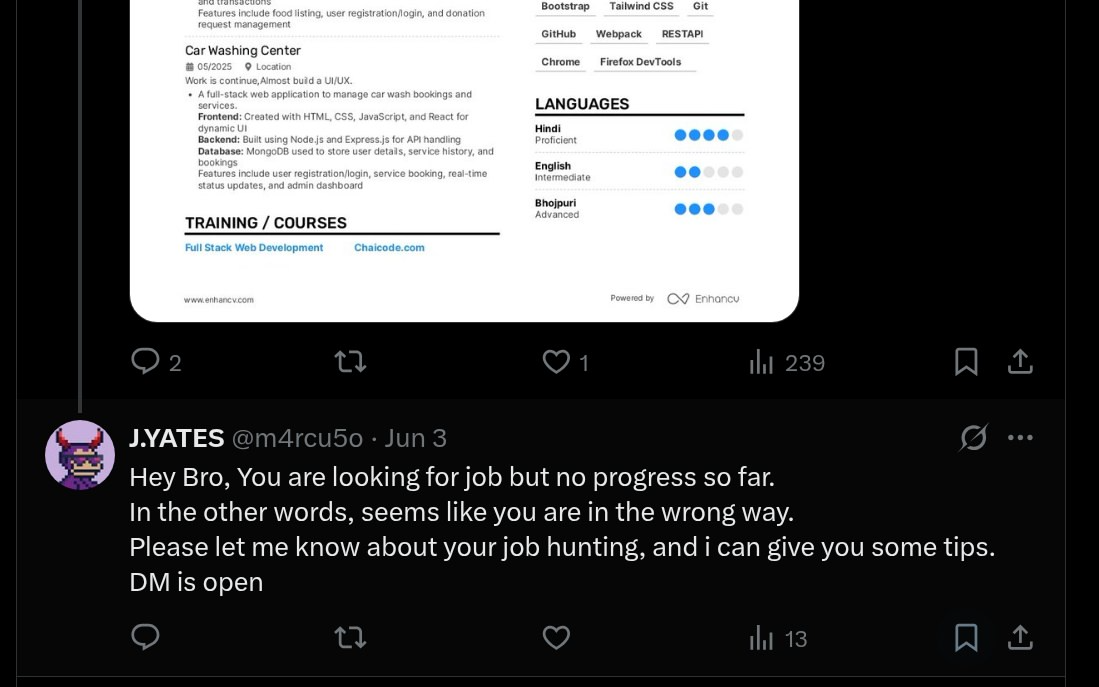
We can also see a lot of ‘credibility boosting’ projects contained in m4rcu5o’s portfolio.
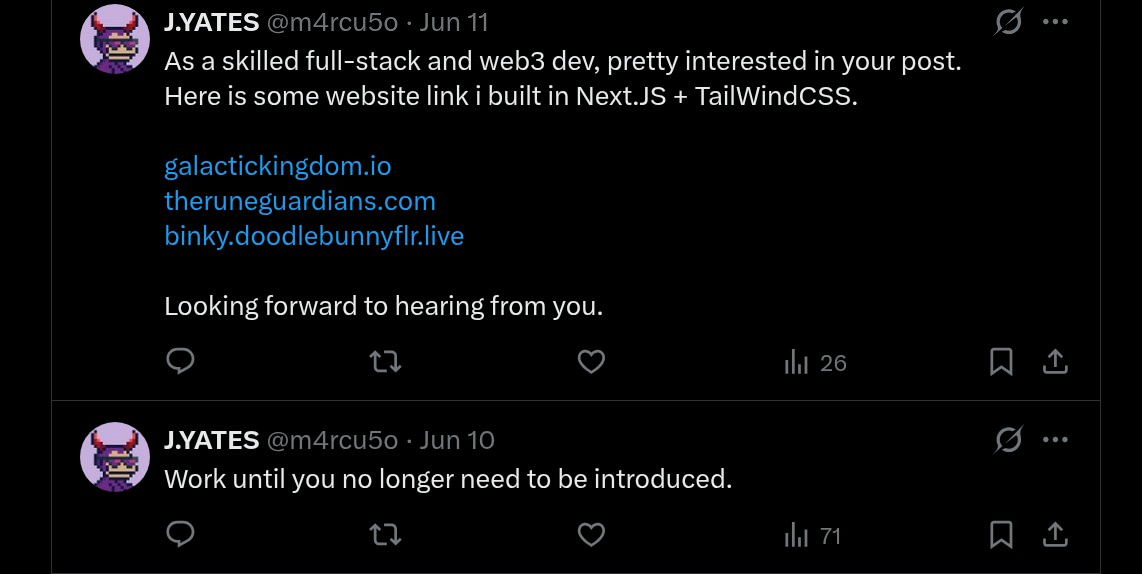
As well as some efforts for what is probably a facilitator search.
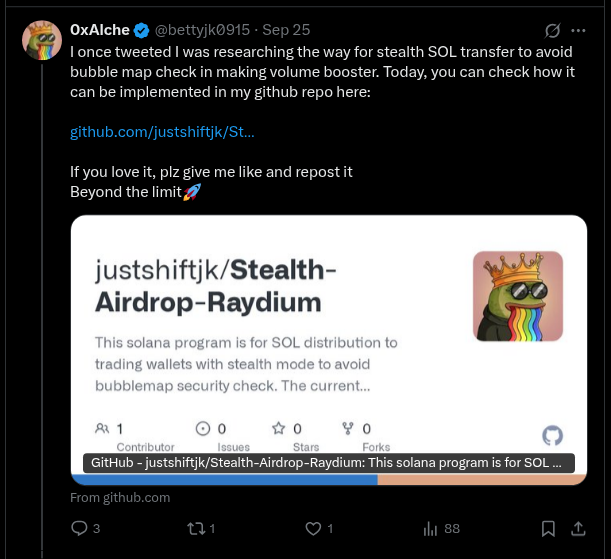
justshiftjk
The original HyperBuildX e-mail was defined as hyperbuildx@adamglab.dev before being changed to admin@hyperbuildx.com. “Adam Glab” is a known identity of a DPRK IT Worker posing as a Polish citizen persistently looking for job engagements in the blockchain space. https://adamglab.dev/ was a portfolio justshiftjk was using.
Github: https://github.com/justshiftjk
Other names: 0xAlche, infinite0731, bettyjk0915
E-mail: adamglab0731.pl@gmail.com
Twitter: https://x.com/bettyjk0915
Telegram: @bettyjk_0915
Youtube: https://www.youtube.com/@justshiftjk
We can see the HyperbuildX organization recommending justshiftjk for a job.
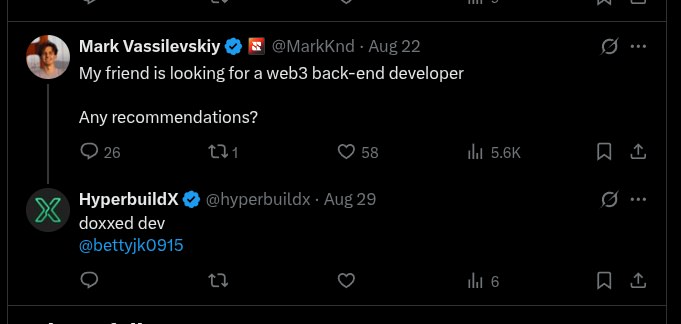
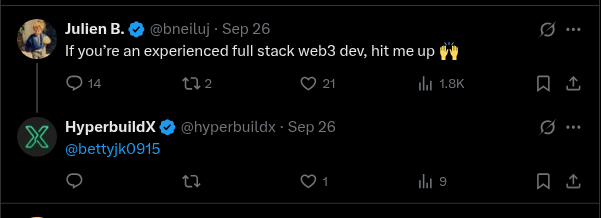
Justshiftjk himself is self-promoting some extremely specific ideas:
Cornel-pe
Github: https://github.com/cornel-cp
E-mail: keigo263129@outlook.ie
Twitter: https://x.com/cornel_pe
Cornel-pe’s account is also receiving ‘boosts’ on Twitter from 0xMuseNine, who we discussed as one of the m8s-lab members and an account closely connected to Hyperbuildx.
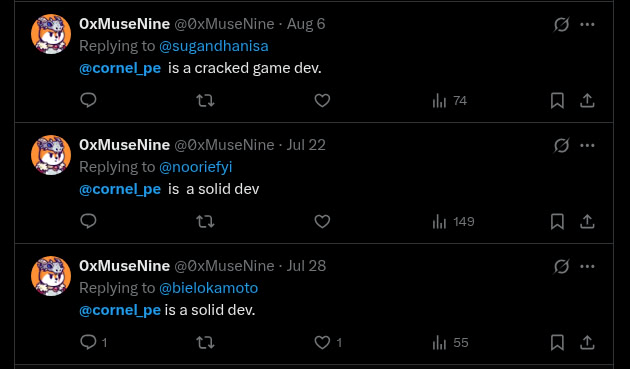
Cornel also seems to operate his own project at https://futuresea.fun. It’s not uncommon for IT Workers to launch their own platforms; it lends them additional credibility and provides a hub to potentially spread malicious code as well as conduct a rug-pull operation if enough velocity is gained. Most such projects are spun from endlessly forked repositories and sprinkled with some simple UI changes and re-branding.
0xOpsDev
Github URL: https://github.com/0xopsdev
Other names: ZireaelGit, MinionGit, meta0xflip
E-mail: nelo.labhart@gmail.com
On-chain: 0x7a87c66718255c5be3c0607e134592d9a8bdb32c
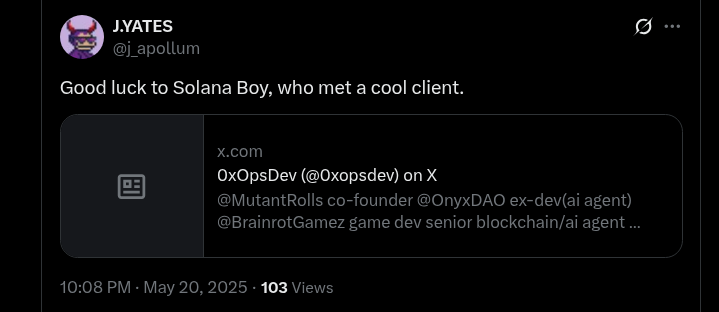
What’s most interesting about 0xopsdev is one of the traces of his past engagement where he complains about not getting paid, thus revealing one of his wallets. The tactic of harassing employers for due payment, regardless of most likely being kicked out of the company for being a DPRK IT Worker, is something we see commonly. Although, it’s also worth noting that DPRK IT Workers are sometimes victims themselves, being scammed out of a salary.
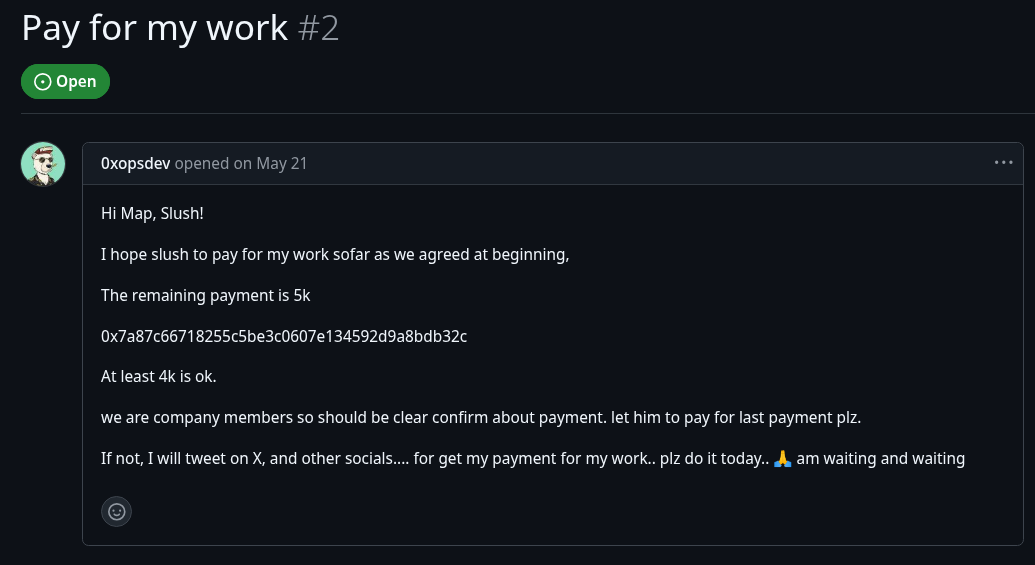
The address provided has a long history of receiving and sending payments.
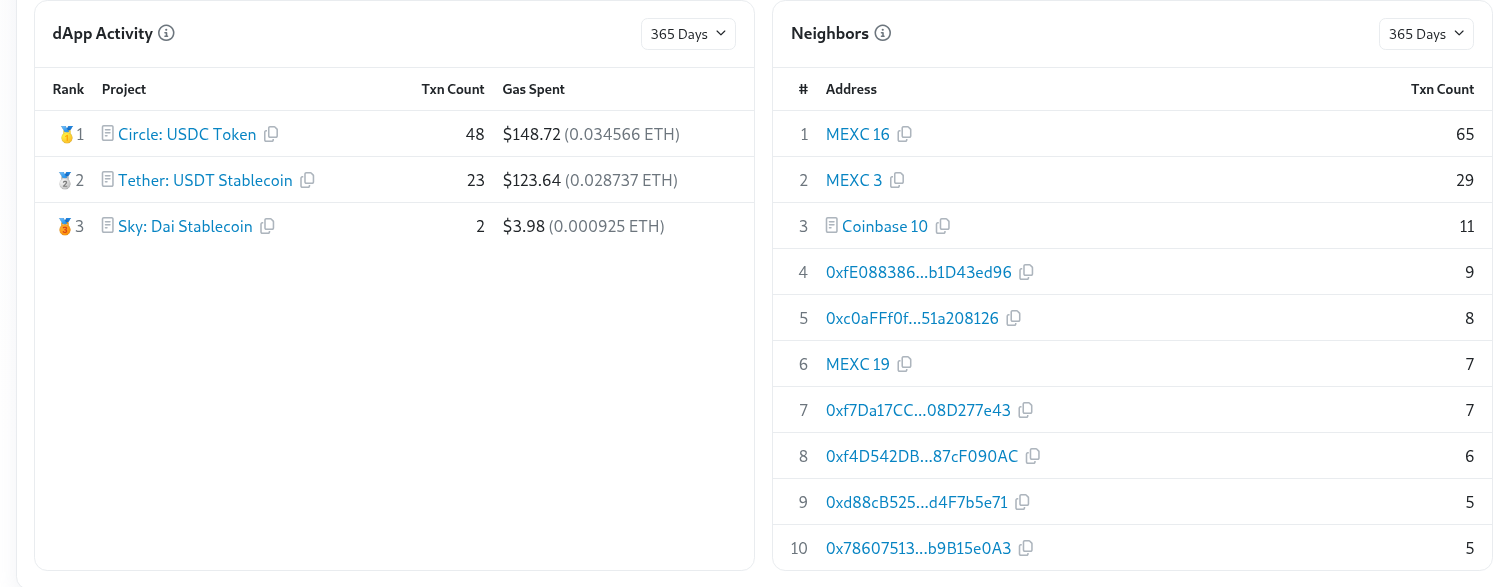
Other DPRK IT Workers in the orbit of HyperbuildX
g0drlc
A member of m8s-lab can also be found heavily connected to HyperBuildX.
Github URL: https://github.com/g0drlc
E-mails: robinhood97110@gmail.com, utommy.abs@gmail.com
Other Names: G0drlc, Tommy Ericsson, g0drlc, temric
Twitter: https://x.com/xg0drlc
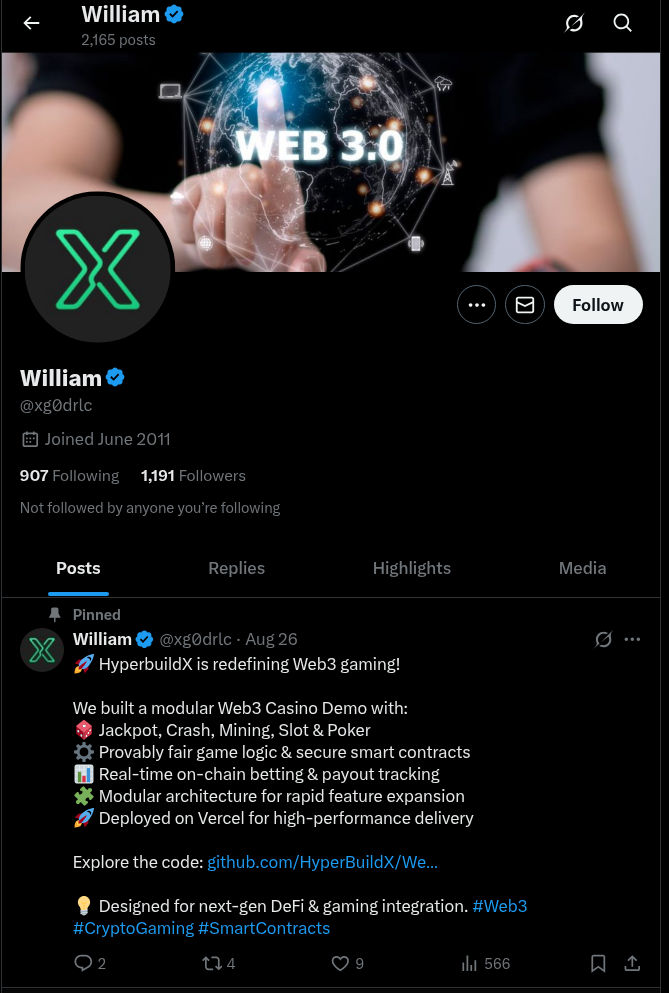
g0drlc is also engaged in some co-operation with cornel-cp, who is a part of HyperbuildX.
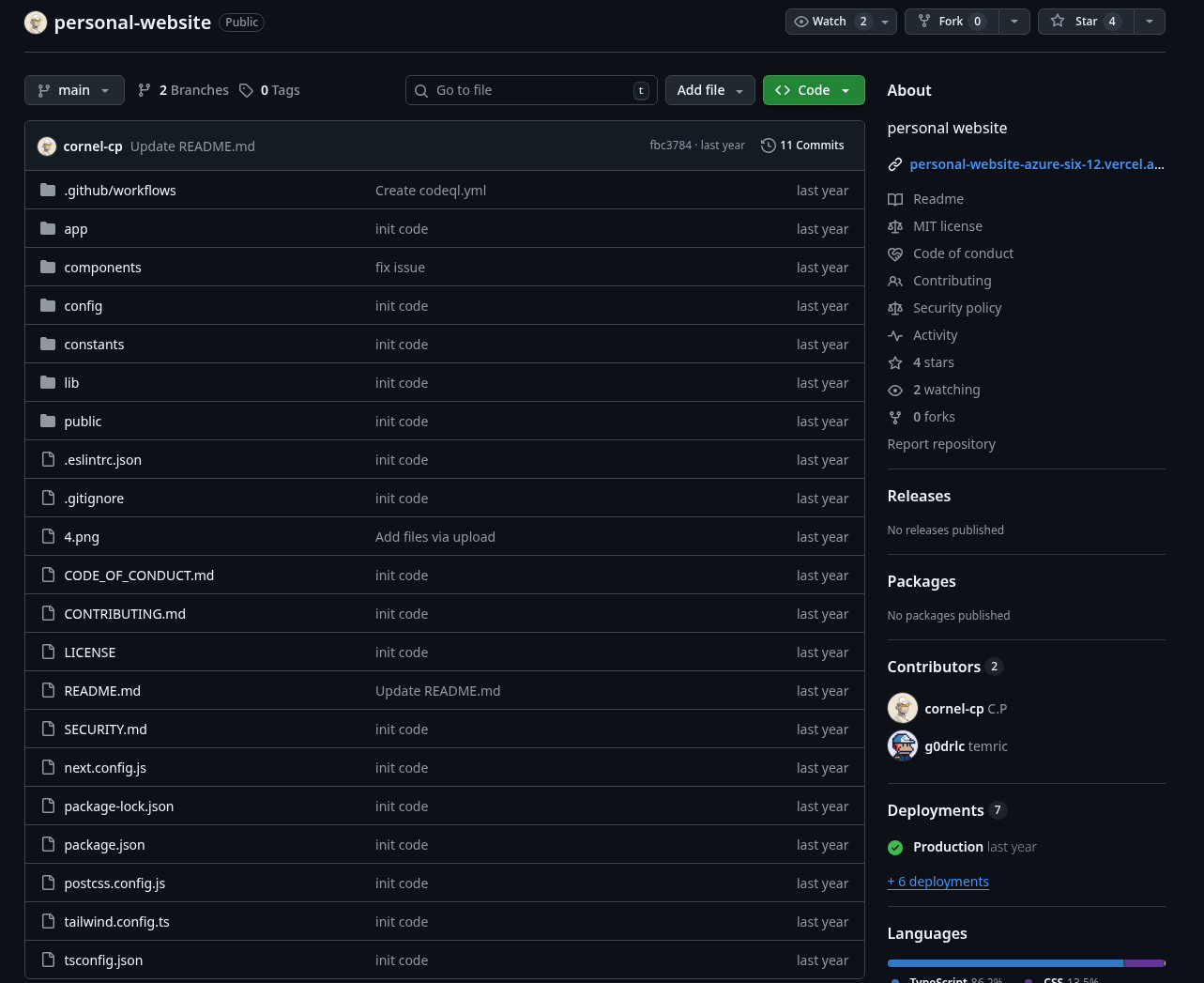
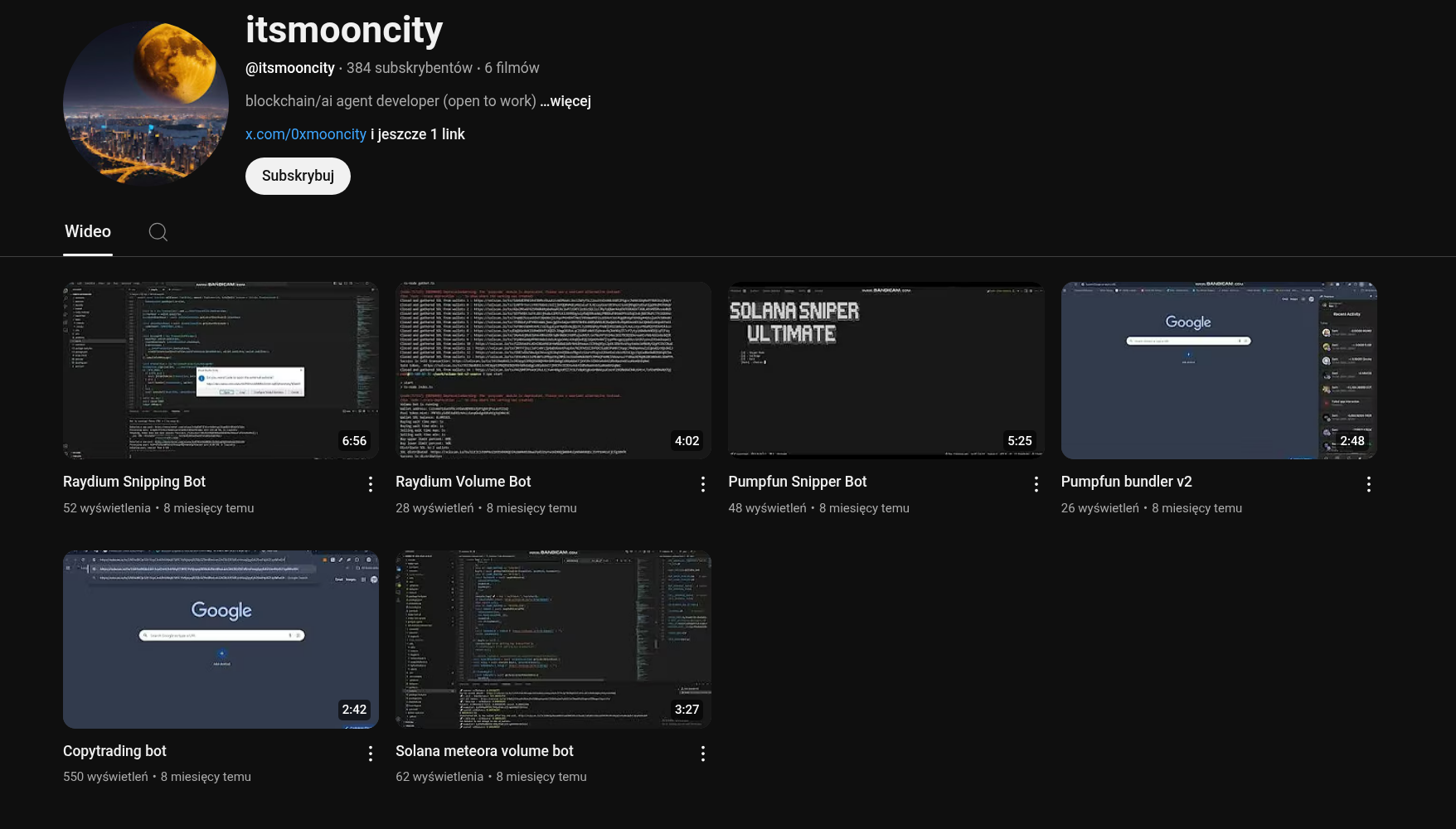
0xMooncity
Boosted by the same bot accounts that are advertising HyperbuildX developers. 0xMooncity is most likely the other g0drlc identity.
Github URL: https://github.com/0xMooncity
E-mails: hellomooncity@gmail.com, shaina42mcdermottjgv@hotmail.com
Portfolio: https://www.mooncity.io
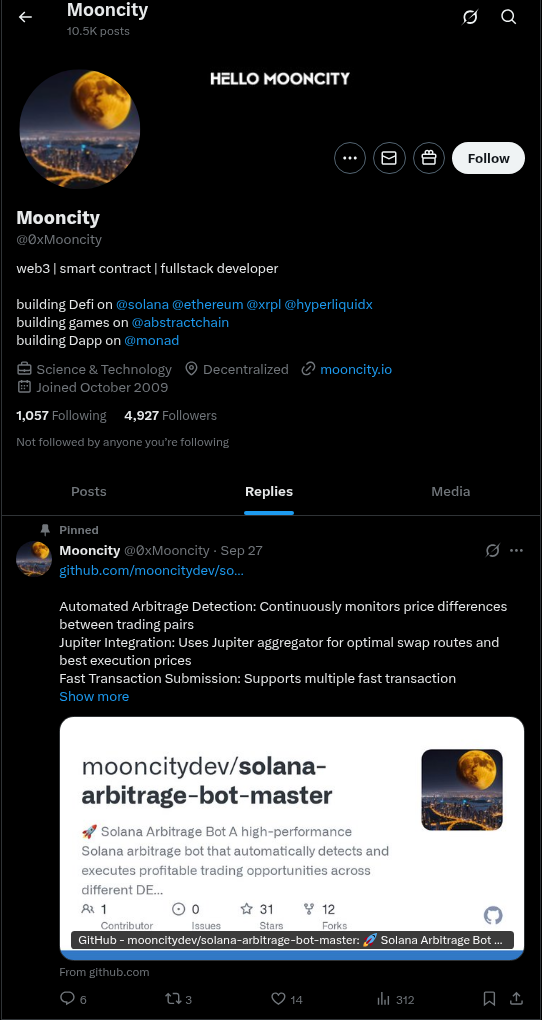
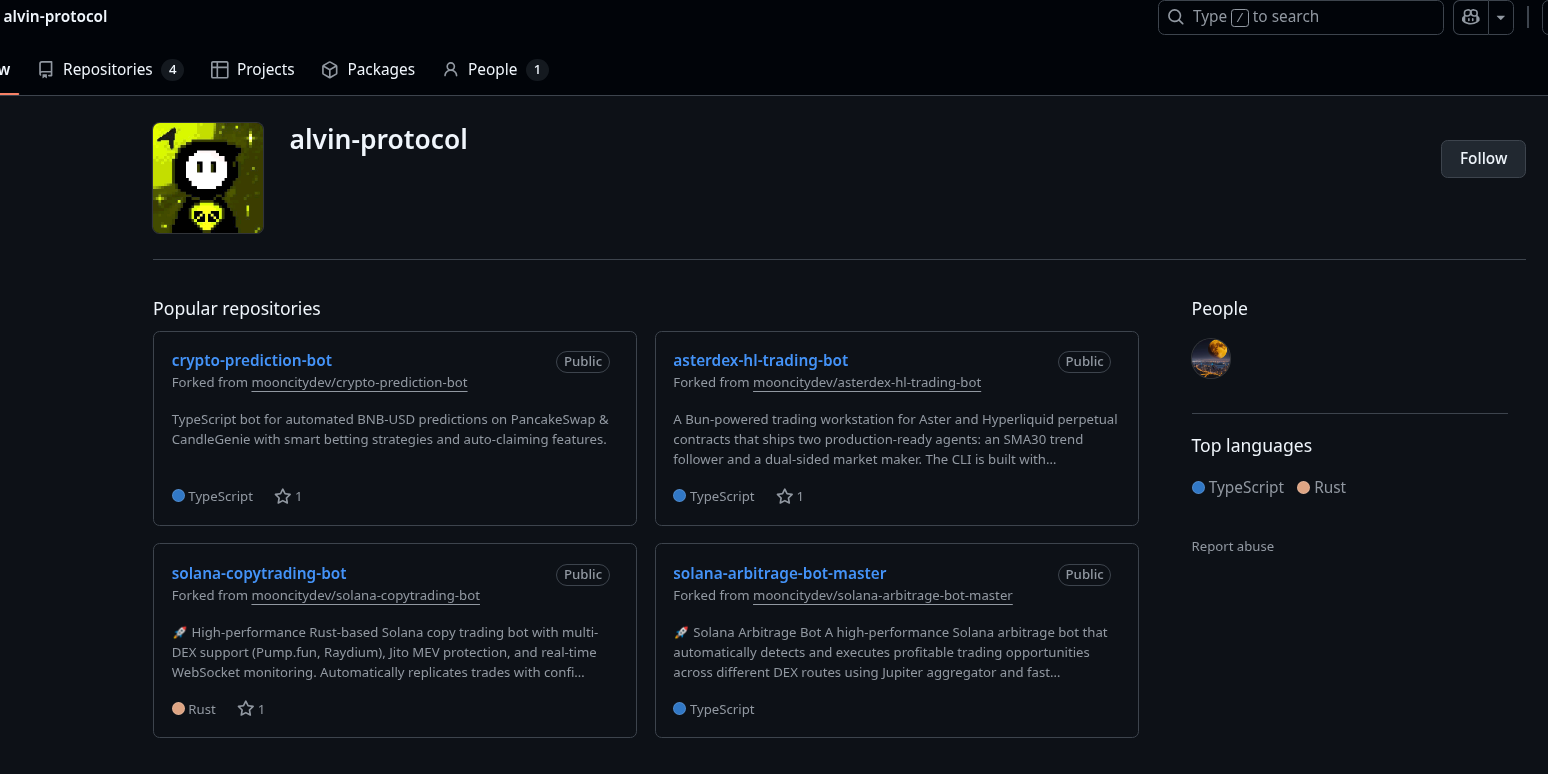
0xMooncity also started to operate his own organization in the meantime, following exactly the same TTPs, but on a smaller scale.
Summary
There are definitely more active DPRK-operated Github organizations. As discussed, the scale of these varies; m8s-lab and hyperbuildx are two of the biggest we encountered and where maintenance efforts continued for over a year. This indicates some success rate in such deployments, as DPRK IT Workers are incentivized to only work on projects they can ultimately monetize. By looking at some of the engagements Hyperbuildx had, we were able to spot answers from large and legitimate projects, unaware they were responding to DPRK operations. This alone may be considered a success by IT Workers as it allows them to gain an initial foothold and the attention of projects they might be interested in attacking (through the regular IT Worker scheme or otherwise) further on.
Some of the recommendations we can issue right now are:
- Do not rely on follower count, activity, or social media presence as the only way to verify credibility. DPRK IT Workers may spend a year working on a “fake” protocol they’ll later use to make themselves appear more credible in your eyes.
- Side-projects are a great way to evaluate your candidates, but DPRK IT Workers have turned this to their own advantage and will actively operate many different, sometimes professional-looking, projects.
- Do not engage with projects and accounts whose origins you are unsure of. Do not follow back blindly; Hyperbuildx was actively asking for follow-backs from reputable accounts with some success.
- DPRK IT Workers are not only individuals. As discussed, you may get an offer from a whole “DPRK-run” company.
- There is a large network of DPRK-operated accounts with a significant history of activity on Twitter; these are used to promote projects (operated by them or other DPRK teams), farm engagement, and even for open-source development.
- Suddenly suspended accounts are always a red flag for anonymous operators. Similarly, DPRK IT Workers are known to claim ‘being hacked’ as a reason for changing their identity. The real reason is most often being discovered as a DPRK operative by another project or some other malicious campaign gone wrong connecting back to their identity.
Indicators of Compromise (IOCs)
Organizations
- m8s-lab
- HyperbuildX
Emails
admin@hyperbuildx.comadamglab0731.pl@gmail.comapollum.today@gmail.comhellomooncity@gmail.comhudes0112@gmail.comhyperbuildx@adamglab.devkeigo263129@outlook.comkeigo263129@outlook.iematthiasli.mt@gmail.commufasa030831@gmail.comnailrusty.dev@gmail.comnelo.labhart@gmail.comrobinhood97110@gmail.comshaina42mcdermottjgv@hotmail.comutommy.abs@gmail.com
GitHub Accounts
- AnotherRusty
- apollotoday
- cornel-cp
- g0drlc
- justshiftjk
- m4rcu5o
- microgift88
- 0xMooncity
- 0xopsdev
- XTruebliss
Twitter/X Accounts
- @bettyjk0915
- @cornel_pe
- @j_apollum
- @m4rcu5o
- @0xMuseNine
- @x_fivefingers
- @x__rusty (suspended)
- @xg0drlc
Websites & Portfolios
https://adamglab.dev/https://futuresea.funhttps://www.matthiasli.com/https://www.mooncity.iohttps://calendly.com/nailrusty-dev/30min
Telegram Accounts
- @bettyjk_0915
- @anotherrusty (https://t.me/anotherrusty)
- idioRusty (https://t.me/idioRusty)
- itsmyturn93
YouTube Channels
https://www.youtube.com/@justshiftjk
On-chain Wallets
0x7a87c66718255c5be3c0607e134592d9a8bdb32c
Discord Accounts
- rusty102 / 397440130744320035
Known Aliases & Fake Names
- 0xAlche
- Adam Glab
- Adrian
- AnotherRusty
- Apollum
- bettyjk0915
- Cornel
- G0drlc
- Hudesdev
- husreodev
- infinite0731
- MacSolDev
- Mathias Li
- Matthias Li
- Matthias Tovar
- meta0xflip
- MinionGit
- MtBotDev
- PupSol
- rusty015
- rustynail015
- SolMatts
- Solust_Rusty
- temric
- Tommy Ericsson
- ZireaelGit

