Here’s an interesting mystery for you all involving a DPRK IT worker (*turned hacker).
Let’s start with a rather unusual victim: @wavesprotocol, a project involved in a $500M heist in 2024.
Discovery
During routine scanning for DPRK-related GitHub activity, we found an active North Korea-related account involved with Keeper-Wallet (a Waves wallet Chrome extension) development. However, it was not the usual scenario of freelance-type engagement we often observe.
Keeper-Wallet is a child project of Waves Protocol, an ecosystem-specific wallet that was being developed by the Waves team before their massive rug pull.
First of all, the Keeper-Wallet organization was inactive until 3 weeks ago. The last (non-DPRK) commit was pushed in August 2023. Suddenly, some repositories started to receive commits in May 2025. These were mostly dependency updates in npm/yarn. On its own, this was slightly weird (beyond Waves’ reputation), but not outright alarming, until…
Compromise
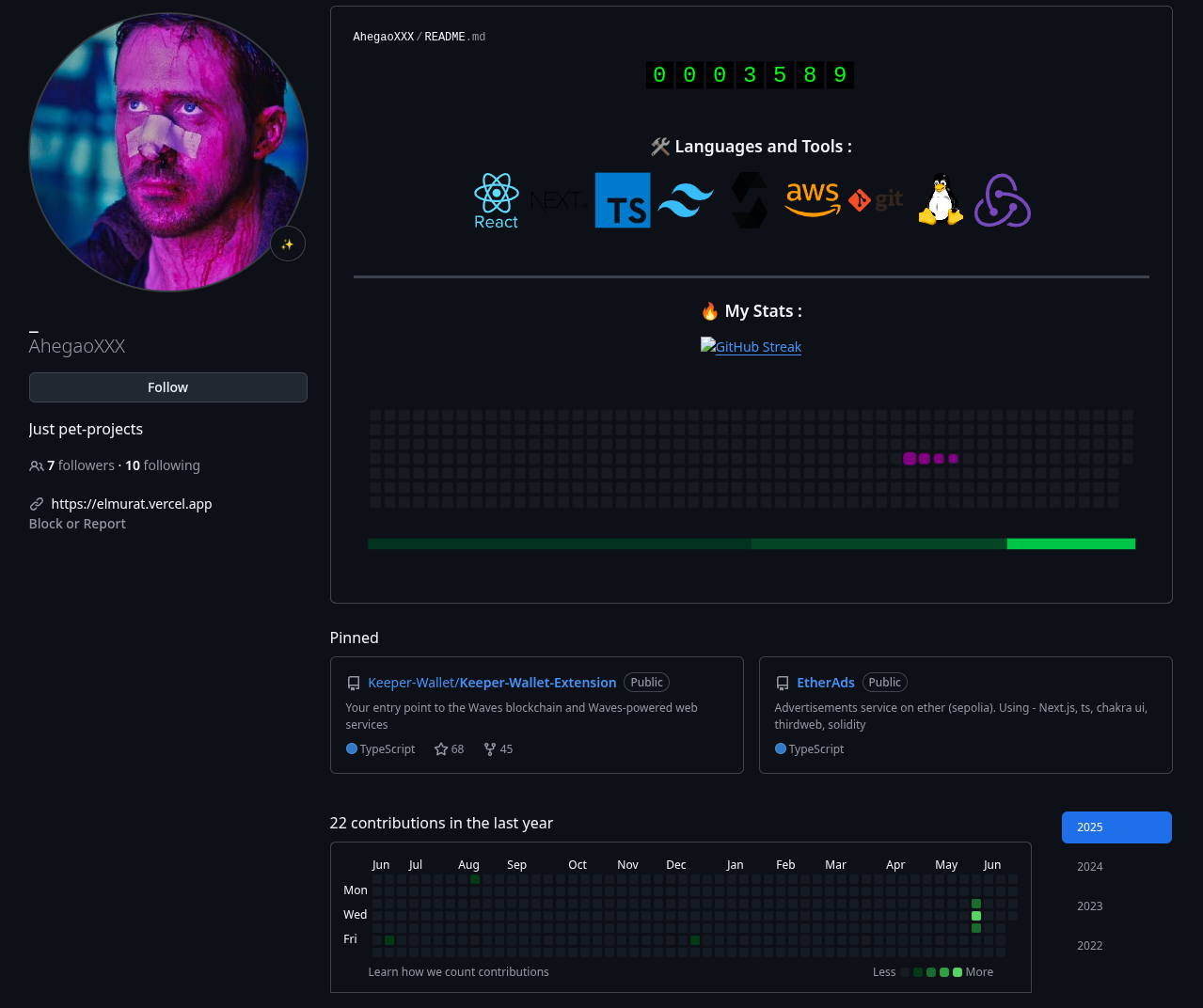
We noticed the account performing these updates has enough privileges to create new repositories, open branches, and trigger releases (including npm releases!) - basically, it had full control over the Keeper-Wallet organization. And we believe the account in question, https://github.com/AhegaoXXX, is connected to DPRK IT worker operations. A rare, but not impossible cross over we sometimes observe.
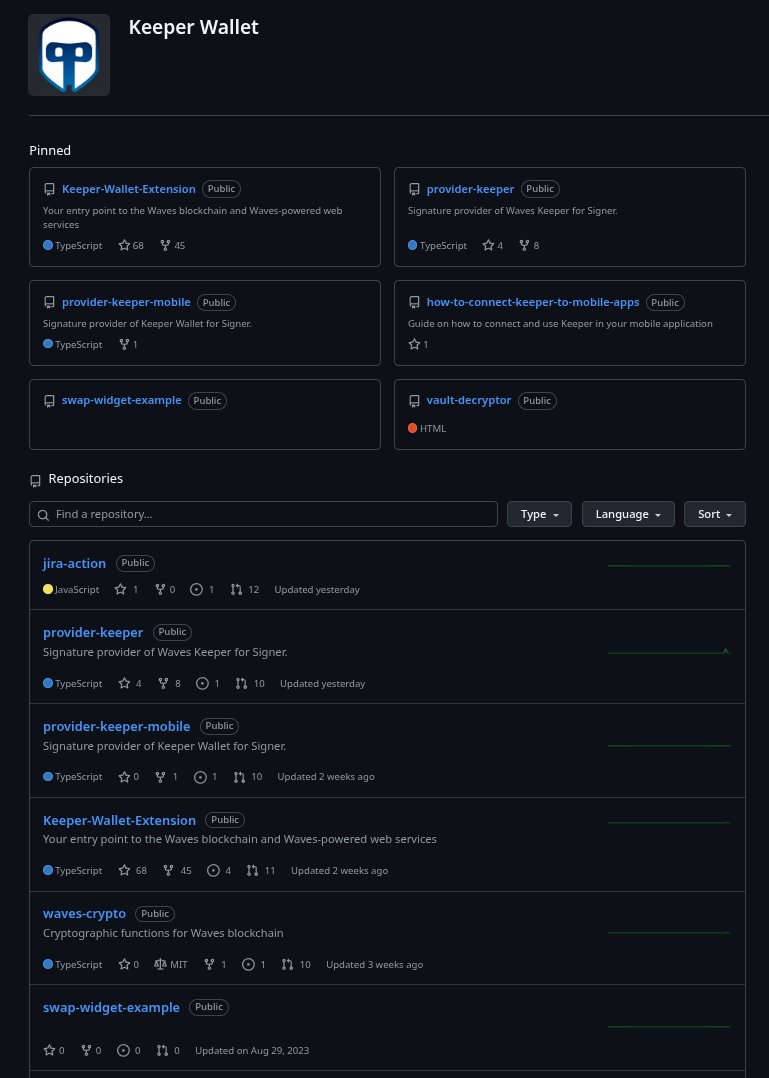
Screenshot of the Keeper-Wallet organization page. Notice the sudden updates across the entire organization within the last 3 weeks.
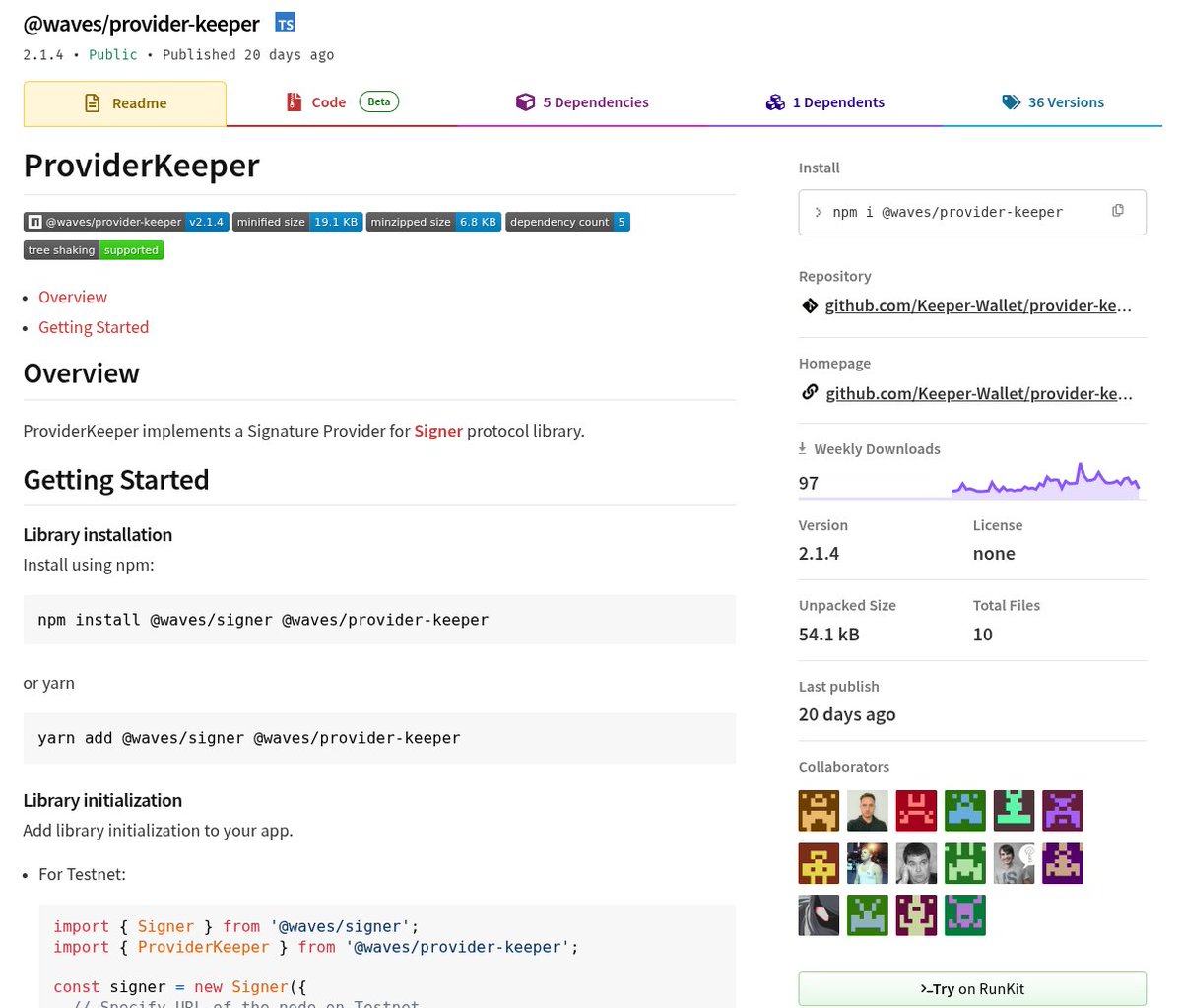
Updated Keeper-Wallet dependency. Notice the name still points to @waves, while the code is read from the /Keeper-Wallet organization. Additionally, the last non-DPRK-related update was to version ‘2.0.9’ on ‘2023-08-31T02:45:26.208Z’. AhegaoXXX triggered the new release of ‘2.1.4’ on ‘2025-05-29T07:54:28.084Z’ - a gap of almost two years.
That’s not all. One of the most interesting code changes happens in Keeper-Wallet/Keeper-Wallet-Extension. AhegaoXXX pushed a rather unusual update targeted at exfiltrating the wallet’s logs and errors to an external database. Besides being privacy-unfriendly, it’s most likely outright malicious - the goal is to log wallet keys or mnemonics. The branch is still unmerged, and a new release has not yet been triggered.
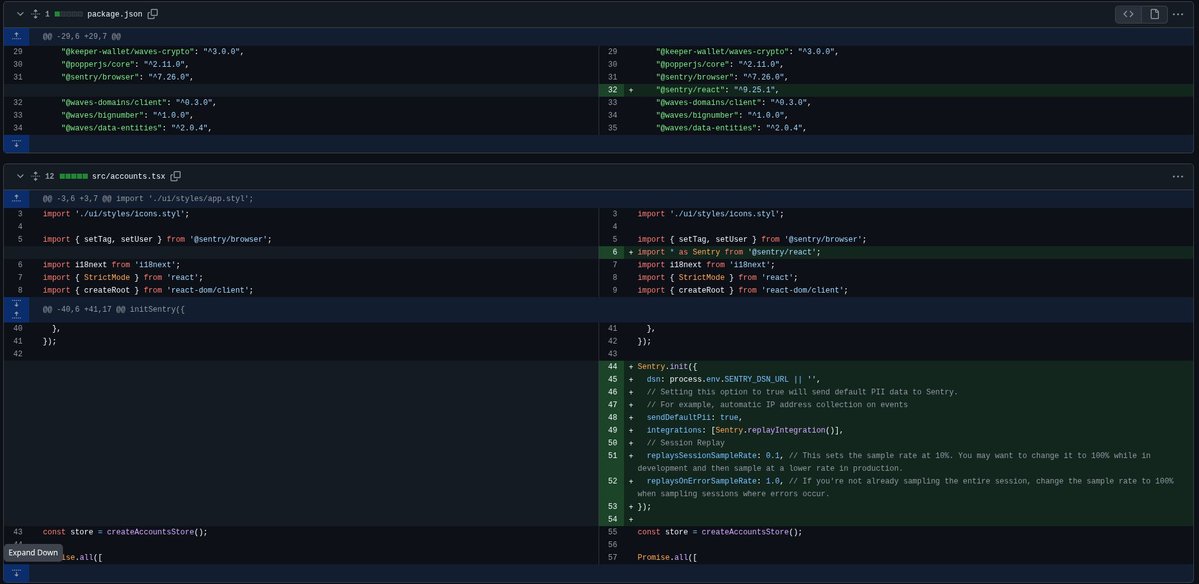
The only meaningful change to any of the repositories is malicious in nature.
Account Takeover
One last thing. We suspect there’s some degree of account takeover happening in the background. We found a few of the /wavesprotocol repositories redirecting to /Keeper-Wallet. This is a behavior that must be triggered from within the /wavesprotocol organization by a privileged account. Two examples:
wavesplatform/provider-keeper ->(redirects to)-> Keeper-Wallet/provider-keeper
wavesplatform/waveskeeper-types ->(redirects to)-> Keeper-Wallet/waveskeeper-types
This led us to run npm view on the latest release of provider-keeper (2.1.14), where we can see that the actual publisher is “msmolyakov-waves - msmolyakov@web3tech.ru” and not “AhegaoXXX - akaredover@gmail.com”. Maxim Smolyakov’s account is most likely compromised but still has enough privileges from his time at the Waves protocol. The last ‘legitimate’ activity of msmolyakov on GitHub was also in 2023; accepting the new Keeper-Wallet release is the only action msmolyakov has taken in the last two years. It’s extremely likely that more accounts under the web3tech.ru domain are compromised, as a few more packages related to maintainers with email addresses on this domain have suddenly become active.
An interesting tidbit is that the North Koreans do not seem to care at all about using compromised Russian accounts - something that usually seems to be a “no-no” for Russia-based black hats (which North Koreans often are, as well).
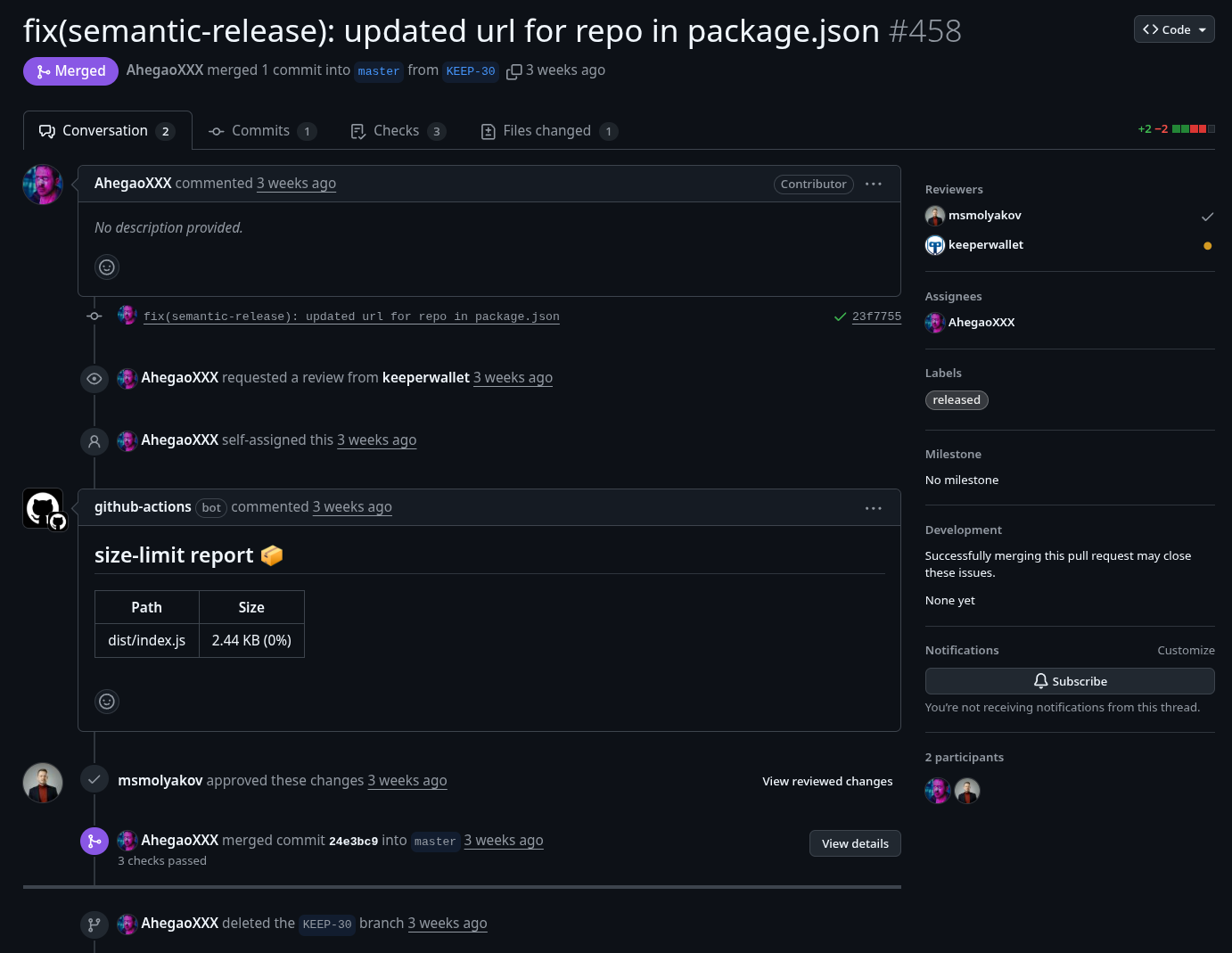
msmolyakov - a potential account takeover victim- accepts the PR, triggering a new release within 4 minutes of AhegaoXXX opening it.
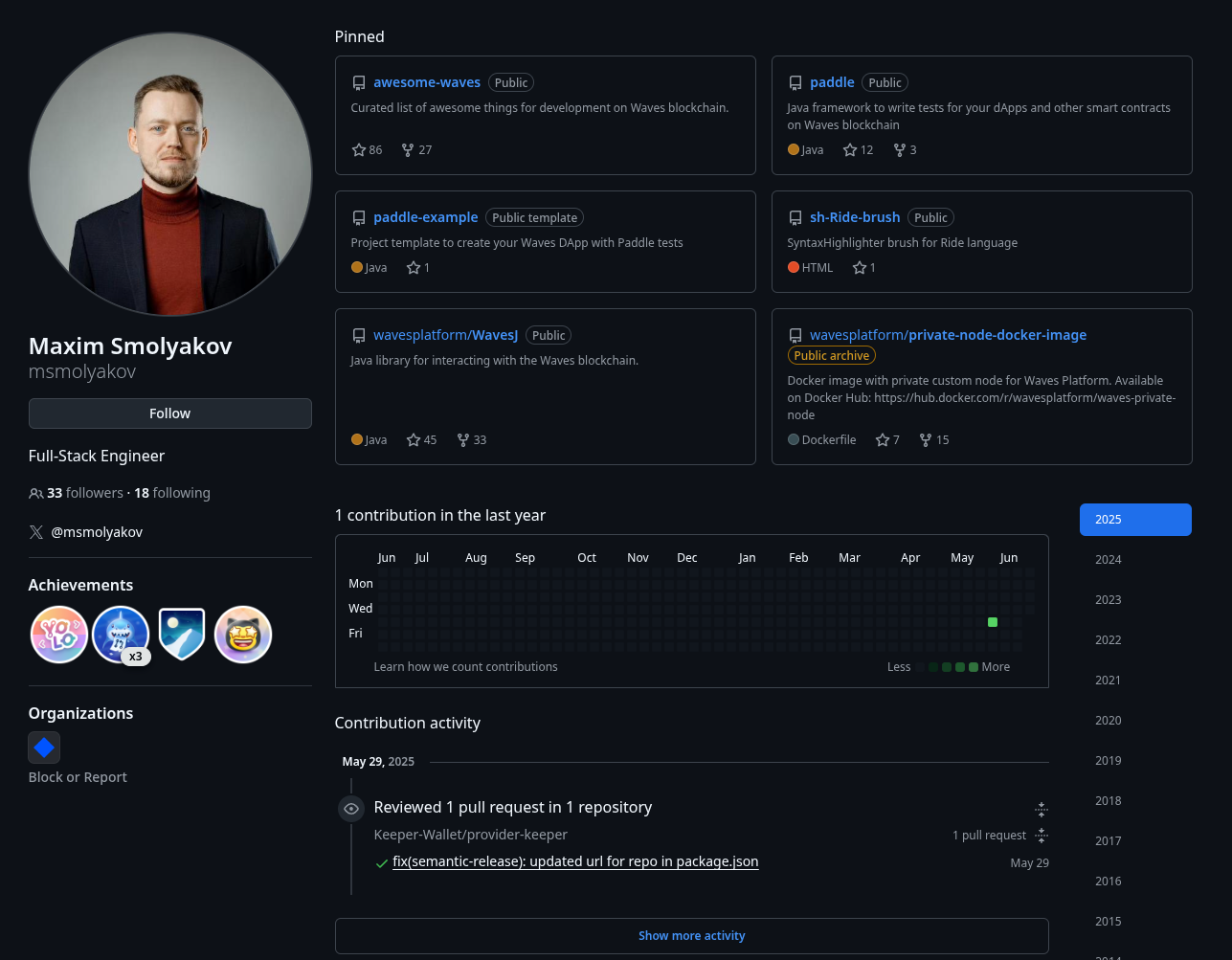
Maxim Smolyakov’s GitHub account has been inactive for an extended period, suggesting AhegaoXXX is most likely in control of it.
It’s worth noting that a few more packages where msmolyakov-waves is one of the publishers are also getting recent updates:
- https://www.npmjs.com/package/@waves/waves-transactions
- https://www.npmjs.com/package/@waves/protobuf-serialization
- https://www.npmjs.com/package/@waves/bignumber
- https://www.npmjs.com/package/@waves/provider-keeper
- https://www.npmjs.com/package/@waves/provider-metamask
- https://www.npmjs.com/package/@waves/node-api-grpc
Here you have it: a mildly interesting crossover between regular DPRK IT worker operations and a potential DPRK hacking team. The motivation is unknown. As is, the ‘attack’ is not yielding any results, although Keeper-Wallet dependencies are still sporadically downloaded from the npm registry. What complicates this case is the nature of the Waves Protocol, which is itself entangled in a massive fraud allegation. This is why we decided to address the issue publicly instead of notifying the company. It is unadvisable for anyone to use Waves, even without the DPRK being implicated in its development and/or hacking.
Safety Measures
We’ll skip the usual warning about DPRK IT workers, as this case is slightly different. What’s relevant for your organization is the proper management of access controls for important parts of your code-related infrastructure.
- Monitor your contributors’ access and privileges to your GitHub organization. Periodically purge inactive members and revoke their privileges.
- Monitor the activity of your contributors, especially privileged ones. What actions are they taking in relation to your organization? Are they transferring or renaming repositories? Are they creating redirects? Are they pushing new updates to any of your packages? Do they trigger some releases?
- Map your contributors’ access to secondary platforms like NPM registries or Docker hubs. In case of an account takeover, an attacker may gain access to push malicious changes into your code supply chain stack.
IOCs:
- https://github.com/AhegaoXXX : akaredover@gmail.com: AhegaoXXX : Elmurat Dzhumabaev
- https://github.com/Keeper-Wallet (Compromised organization)
- https://github.com/Keeper-Wallet/Keeper-Wallet-Extension
- https://github.com/Keeper-Wallet/provider-keeper
- https://github.com/wavesplatform
- https://www.npmjs.com/~msmolyakov-waves
- https://web3tech.ru/ (potentially compromised domain/mx)
- https://github.com/msmolyakov (Account that’s taken over) : Maxim Smolyakov
- https://chromewebstore.google.com/detail/keeper-wallet/lpilbniiabackdjcionkobglmddfbcjo (Potentially vulnerable Chrome Extension)
- https://www.npmjs.com/package/@waves/provider-keeper (Compromised npm package)

